Custom kernel to match chroot, efistub for embedded bootloader and RO sandbox for root only [Solved as incompatible]
Posted: Mon Mar 10, 2025 11:12 am
The x299 Im using is a misfit from what is classed as normal and has special needs, as in this pc will be used for cad and my old x79 will be running the cam. I am trying to set up gentoo or liguros to run on this x299 but need to do custom stuff to it, to fit my needs and wants for a operating system.
So need a quick to launch and setup recovery os to service this, MX linux fits what I need and this tool is one example. This chroot tool would keep from needing hackery with !bin-bash to do the same job, this tool dose it cleaner and easier.
The theme I use is this border set and a color palette I made almost a decade ago, the icon and cursor set is all that has change based on what works with a given os. So what to use a copy of my current home with mx linux and dont want it to be RO. There is issues caused by the newer kwin and need to find settings for stuff, if I cant figure these out I will ask in another post.
https://store.kde.org/p/998870
I grabbed this MX-23.3 LXQt 1.3 Respin to use, since has lxqt that works like the old ked3.5/4. The newer kde5/6 plasma works with my theme but has more bloat than Id like, and want to keep things the same as what will be in use with the working os. This is a x32 iso and not sure if that will give issues with a x64 only kernel, if need to use a different respin will do so. Only change I made is removed xfce and replaced it with kwin-x11, since what I want for display manager.
viewtopic.php?t=80729
As for the special needs of this x299 board, it has its own embedded boot loader that is very picky as to what it will list. I have had issues getting this to like grub but the way mx linux makes it, it can be found but there is two instances of it. So MX linux gives a proper example of setting up a ESP partition but dont see reason to be chain loading boot loaders, I have been trying to setup gentoo or liguros for efistub and no systemd, but that means doing a bunch of custom stuff. Has efistub been tried for MX linux and is there any documentation on it?

I am using a custom kernel for the gentoo or liguros that will be build in chroot using MX linux, the kernel needs to match between the two so things are built correctly and not give error. I fixed this ebuild and got it mostly working, it was using debian source but I changed that to a custom one to sort out the hardened patches that was in this.
https://github.com/1mouse3/liguros-xxx/ ... -r1.ebuild
This port of the GrapheneOS kernel is up to date and has those patches already applied, so is what I used over the given patch set.
https://github.com/anthraxx/linux-hardened
Based on what I found in how a debian kernel works, I made these tar balls for use in that ebuild. Debian uses a ASOP kernel and runs its own patch set to change that state, but here the ASOP is replaced by the GrapheneOS source. I have the 6.1.27_p1-r1 patch set here since the 6.1.124_p1-r1 patch set was not available when I made this.
To get this change of source to work, I had to make this patch set to make the debian patches happy.
https://github.com/1mouse3/liguros-xxx/ ... ne-patches
So should be a simple swap of stuff and addition of a patch to get this working in a debian .deb, but not too sure on that. Found this article on doing what I want but needs "deb-src" for the first step that is not a available package, and not sure what else would give issues in this.
https://quantum5.ca/2021/08/04/building ... ckporting/
And this is the config I what to use for this kernel, it is setup for use with this board and has hardened changes.
https://github.com/1mouse3/liguros-xxx/ ... es/.config
So the finale question is over RO snadbox for root only and not home, home is to be copy of current used. Squashfs dose the RO sandbox and MX linux is using this, issue is I dont know the correct terms used for such. Reason for this is that if the system crashes when building the OS in chroot, it will corrupt data that is RW for root and dont want this to occur since will entail a rebuild. So would like MX linux to be setup like this...
Code: Select all
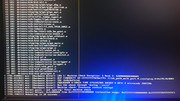
Snapshot created on: 20240527_0909
System:
Kernel: 6.1.0-31-amd64 [6.1.128-1] arch: x86_64 bits: 64 compiler: gcc v: 12.2.0
parameters: BOOT_IMAGE=/boot/vmlinuz-6.1.0-31-amd64 root=UUID=<filter> ro quiet splash
Desktop: LXQt v: 1.3.0 info: lxqt-panel wm: kwin_x11 vt: 7 dm: SDDM Distro: MX-23.5_x64
Libretto May 19 2024 base: Debian GNU/Linux 12 (bookworm)
Machine:
Type: Desktop Mobo: EVGA model: X299 FTW K v: 1.0 serial: <superuser required>
UEFI: American Megatrends v: 1.29 date: 11/22/2021
CPU:
Info: model: Intel Core i9-7940X bits: 64 type: MT MCP arch: Skylake gen: core 7 level: v4
note: check process: Intel 14nm family: 6 model-id: 0x55 (85) stepping: 4 microcode: 0x2007006
Topology: cpus: 1x cores: 14 tpc: 2 threads: 28 smt: enabled cache: L1: 896 KiB desc: d-14x32
KiB; i-14x32 KiB L2: 14 MiB desc: 14x1024 KiB L3: 19.2 MiB desc: 1x19.2 MiB
Speed (MHz): avg: 1378 high: 2200 min/max: 1200/4400 scaling: driver: intel_cpufreq
governor: ondemand cores: 1: 1200 2: 1200 3: 1200 4: 1200 5: 1400 6: 1200 7: 1500 8: 1200 9: 1200
10: 1829 11: 1200 12: 2200 13: 1335 14: 1200 15: 1200 16: 1200 17: 1200 18: 1200 19: 1600
20: 2000 21: 1200 22: 1700 23: 1200 24: 2000 25: 1200 26: 1200 27: 1324 28: 1301
bogomips: 173599
Flags: avx avx2 ht lm nx pae sse sse2 sse3 sse4_1 sse4_2 ssse3 vmx
Vulnerabilities:
Type: gather_data_sampling mitigation: Microcode
Type: itlb_multihit status: KVM: VMX disabled
Type: l1tf mitigation: PTE Inversion; VMX: conditional cache flushes, SMT vulnerable
Type: mds mitigation: Clear CPU buffers; SMT vulnerable
Type: meltdown mitigation: PTI
Type: mmio_stale_data mitigation: Clear CPU buffers; SMT vulnerable
Type: reg_file_data_sampling status: Not affected
Type: retbleed mitigation: IBRS
Type: spec_rstack_overflow status: Not affected
Type: spec_store_bypass mitigation: Speculative Store Bypass disabled via prctl
Type: spectre_v1 mitigation: usercopy/swapgs barriers and __user pointer sanitization
Type: spectre_v2 mitigation: IBRS; IBPB: conditional; STIBP: conditional; RSB filling;
PBRSB-eIBRS: Not affected; BHI: Not affected
Type: srbds status: Not affected
Type: tsx_async_abort mitigation: Clear CPU buffers; SMT vulnerable
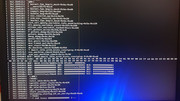
Graphics:
Device-1: NVIDIA GK107 [GeForce GT 740] vendor: eVga.com. driver: nvidia v: 470.256.02 non-free:
series: 470.xx+ status: legacy-active (EOL~2023/24) arch: Kepler code: GKxxx process: TSMC 28nm
built: 2012-18 pcie: gen: 1 speed: 2.5 GT/s lanes: 8 link-max: gen: 3 speed: 8 GT/s lanes: 16
bus-ID: 65:00.0 chip-ID: 10de:0fc8 class-ID: 0300
Display: x11 server: X.Org v: 1.21.1.7 compositor: kwin_x11 driver: X: loaded: nvidia
unloaded: fbdev,modesetting,nouveau,vesa alternate: nv gpu: nvidia display-ID: :0 screens: 1
Screen-1: 0 s-res: 1920x1200 s-dpi: 90 s-size: 542x350mm (21.34x13.78") s-diag: 645mm (25.4")
Monitor-1: DVI-D-0 res: 1920x1200 hz: 60 dpi: 89 size: 546x352mm (21.5x13.86")
diag: 650mm (25.58") modes: N/A
API: OpenGL v: 4.6.0 NVIDIA 470.256.02 renderer: NVIDIA GeForce GT 740/PCIe/SSE2
direct-render: Yes
Audio:
Device-1: NVIDIA GK107 HDMI Audio vendor: eVga.com. driver: snd_hda_intel bus-ID: 5-1:2 v: kernel
pcie: chip-ID: 3842:3100 class-ID: fe01 gen: 3 speed: 8 GT/s lanes: 8 link-max: lanes: 16
bus-ID: 65:00.1 chip-ID: 10de:0e1b class-ID: 0403
Device-2: EVGA NU Audio type: USB driver: snd-usb-audio
API: ALSA v: k6.1.0-31-amd64 status: kernel-api tools: alsamixer,amixer
Server-1: PipeWire v: 1.0.0 status: active with: 1: pipewire-pulse status: active
2: wireplumber status: active 3: pipewire-alsa type: plugin 4: pw-jack type: plugin
tools: pactl,pw-cat,pw-cli,wpctl
Network:
Device-1: Intel Ethernet I219-V driver: e1000e v: kernel port: N/A bus-ID: 00:1f.6
chip-ID: 8086:15b8 class-ID: 0200
IF: eth1 state: up speed: 100 Mbps duplex: full mac: <filter>
Device-2: Qualcomm Atheros Killer E2500 Gigabit Ethernet vendor: Acer Incorporated ALI
driver: alx v: kernel pcie: gen: 1 speed: 2.5 GT/s lanes: 1 port: 2000 bus-ID: 03:00.0
chip-ID: 1969:e0b1 class-ID: 0200
IF: eth0 state: down mac: <filter>
Device-3: Intel Ethernet 10-Gigabit X540-AT2 driver: ixgbe v: kernel pcie: gen: 2 speed: 5 GT/s
lanes: 8 port: N/A bus-ID: 17:00.0 chip-ID: 8086:1528 class-ID: 0200
IF: eth2 state: down mac: <filter>
Device-4: Intel Ethernet 10-Gigabit X540-AT2 driver: ixgbe v: kernel pcie: gen: 2 speed: 5 GT/s
lanes: 8 port: N/A bus-ID: 17:00.1 chip-ID: 8086:1528 class-ID: 0200
IF: eth3 state: down mac: <filter>
Drives:
Local Storage: total: 10.49 TiB used: 66.86 GiB (0.6%)
SMART Message: Unable to run smartctl. Root privileges required.
ID-1: /dev/nvme0n1 maj-min: 259:0 vendor: Crucial model: CT500P2SSD8 size: 465.76 GiB
block-size: physical: 512 B logical: 512 B speed: 31.6 Gb/s lanes: 4 type: SSD serial: <filter>
rev: P2CR048 temp: 33.9 C scheme: GPT
ID-2: /dev/nvme1n1 maj-min: 259:6 vendor: Crucial model: CT500P3SSD8 size: 465.76 GiB
block-size: physical: 512 B logical: 512 B speed: 31.6 Gb/s lanes: 4 type: SSD serial: <filter>
rev: P9CR313 temp: 40.9 C scheme: GPT
ID-3: /dev/nvme2n1 maj-min: 259:7 vendor: Crucial model: CT500P3SSD8 size: 465.76 GiB
block-size: physical: 512 B logical: 512 B speed: 31.6 Gb/s lanes: 4 type: SSD serial: <filter>
rev: P9CR313 temp: 34.9 C scheme: GPT
ID-4: /dev/sda maj-min: 8:0 vendor: Western Digital model: WD80EZZX-11CSGA0 size: 7.28 TiB
block-size: physical: 4096 B logical: 512 B speed: 6.0 Gb/s type: HDD rpm: 5400 serial: <filter>
rev: 0A03 scheme: GPT
ID-5: /dev/sdb maj-min: 8:16 vendor: Western Digital model: WD20EADS-00R6B0 size: 1.82 TiB
block-size: physical: 512 B logical: 512 B speed: 3.0 Gb/s type: N/A serial: <filter> rev: 0A01
scheme: MBR
ID-6: /dev/sdc maj-min: 8:32 type: USB vendor: SanDisk model: USB 3.2Gen1 size: 28.65 GiB
block-size: physical: 512 B logical: 512 B type: N/A serial: <filter> rev: 1.00 scheme: MBR
SMART Message: Unknown USB bridge. Flash drive/Unsupported enclosure?
Partition:
ID-1: / raw-size: 97.66 GiB size: 95.56 GiB (97.86%) used: 10.71 GiB (11.2%) fs: ext4
dev: /dev/sda6 maj-min: 8:6
ID-2: /boot/efi raw-size: 1000 MiB size: 998 MiB (99.80%) used: 288 KiB (0.0%) fs: vfat
dev: /dev/sda8 maj-min: 8:8
ID-3: /home raw-size: 389.65 GiB size: 382.47 GiB (98.16%) used: 52.9 GiB (13.8%) fs: ext4
dev: /dev/sda7 maj-min: 8:7
Swap:
Kernel: swappiness: 15 (default 60) cache-pressure: 100 (default)
ID-1: swap-1 type: partition size: 124.98 GiB used: 0 KiB (0.0%) priority: -2 dev: /dev/dm-0
maj-min: 253:0 mapped: luks-<filter>
Sensors:
System Temperatures: cpu: 43.0 C mobo: N/A gpu: nvidia temp: 40 C
Fan Speeds (RPM): N/A gpu: nvidia fan: 21%
Repos:
Packages: pm: dpkg pkgs: 2548 libs: 1367 tools: apt,apt-get,aptitude,nala,synaptic pm: rpm
pkgs: 0 pm: flatpak pkgs: 0
No active apt repos in: /etc/apt/sources.list
Active apt repos in: /etc/apt/sources.list.d/debian-stable-updates.list
1: deb http://deb.debian.org/debian bookworm-updates main contrib non-free non-free-firmware
Active apt repos in: /etc/apt/sources.list.d/debian.list
1: deb http://deb.debian.org/debian bookworm main contrib non-free non-free-firmware
2: deb http://security.debian.org/debian-security bookworm-security main contrib non-free non-free-firmware
Active apt repos in: /etc/apt/sources.list.d/mx.list
1: deb http://mirrors.rit.edu/mxlinux/mx-packages/mx/repo/ bookworm main non-free
Info:
Processes: 427 Uptime: 15h 24m wakeups: 1 Memory: 62.49 GiB used: 4.74 GiB (7.6%) Init: SysVinit
v: 3.06 runlevel: 5 default: graphical tool: systemctl Compilers: gcc: 12.2.0 alt: 12
Client: shell wrapper v: 5.2.15-release inxi: 3.3.26
Boot Mode: UEFISo need a quick to launch and setup recovery os to service this, MX linux fits what I need and this tool is one example. This chroot tool would keep from needing hackery with !bin-bash to do the same job, this tool dose it cleaner and easier.

The theme I use is this border set and a color palette I made almost a decade ago, the icon and cursor set is all that has change based on what works with a given os. So what to use a copy of my current home with mx linux and dont want it to be RO. There is issues caused by the newer kwin and need to find settings for stuff, if I cant figure these out I will ask in another post.
https://store.kde.org/p/998870
I grabbed this MX-23.3 LXQt 1.3 Respin to use, since has lxqt that works like the old ked3.5/4. The newer kde5/6 plasma works with my theme but has more bloat than Id like, and want to keep things the same as what will be in use with the working os. This is a x32 iso and not sure if that will give issues with a x64 only kernel, if need to use a different respin will do so. Only change I made is removed xfce and replaced it with kwin-x11, since what I want for display manager.
viewtopic.php?t=80729
As for the special needs of this x299 board, it has its own embedded boot loader that is very picky as to what it will list. I have had issues getting this to like grub but the way mx linux makes it, it can be found but there is two instances of it. So MX linux gives a proper example of setting up a ESP partition but dont see reason to be chain loading boot loaders, I have been trying to setup gentoo or liguros for efistub and no systemd, but that means doing a bunch of custom stuff. Has efistub been tried for MX linux and is there any documentation on it?

I am using a custom kernel for the gentoo or liguros that will be build in chroot using MX linux, the kernel needs to match between the two so things are built correctly and not give error. I fixed this ebuild and got it mostly working, it was using debian source but I changed that to a custom one to sort out the hardened patches that was in this.
https://github.com/1mouse3/liguros-xxx/ ... -r1.ebuild
This port of the GrapheneOS kernel is up to date and has those patches already applied, so is what I used over the given patch set.
https://github.com/anthraxx/linux-hardened
Based on what I found in how a debian kernel works, I made these tar balls for use in that ebuild. Debian uses a ASOP kernel and runs its own patch set to change that state, but here the ASOP is replaced by the GrapheneOS source. I have the 6.1.27_p1-r1 patch set here since the 6.1.124_p1-r1 patch set was not available when I made this.
Code: Select all
KERNEL_ARCHIVE="https://www.dropbox.com/scl/fi/isqrcpbld7pk6iln2dt6c/linux_6.1.124.orig.tar.xz?rlkey=kdldkzec29i70aq689yoy2yv2&st=toxjojql&dl=0&raw=1 -> ${KERNEL}"
DEB_PATCH_ARCHIVE="https://www.dropbox.com/scl/fi/bfuyprfhj7cq17dzbruqf/linux_6.1.124-1.debian.tar.xz?rlkey=44pi91kwxa6v8mpnj5i8rcw0n&st=mmnekdpy&raw=1 -> ${DEB_PATCH}"
DEB_DSC_ARCHIVE="https://www.dropbox.com/scl/fi/gaia3pyf5fy3uxn12rv34/linux_6.1.124-1.dsc?rlkey=84johlvp7kd8l093pj9knmdtf&st=9biultvi&dl=0&raw=1 -> linux_${DEB_PV}.dsc"https://github.com/1mouse3/liguros-xxx/ ... ne-patches
So should be a simple swap of stuff and addition of a patch to get this working in a debian .deb, but not too sure on that. Found this article on doing what I want but needs "deb-src" for the first step that is not a available package, and not sure what else would give issues in this.
https://quantum5.ca/2021/08/04/building ... ckporting/
And this is the config I what to use for this kernel, it is setup for use with this board and has hardened changes.
https://github.com/1mouse3/liguros-xxx/ ... es/.config
So the finale question is over RO snadbox for root only and not home, home is to be copy of current used. Squashfs dose the RO sandbox and MX linux is using this, issue is I dont know the correct terms used for such. Reason for this is that if the system crashes when building the OS in chroot, it will corrupt data that is RW for root and dont want this to occur since will entail a rebuild. So would like MX linux to be setup like this...
Code: Select all
HDD-PART-A= source of MX linux root, so it can be updated and remake the USB when needed
HDD-PART-B= ESP boot for HDD-PART-A
HDD-PART-C= copy of current home
USB-PART-A= RO sandbox of MX linux for normal use, would like this to be compressed and to be ran in tempfs since have the ram for that so dont need a large usb that will get hot and degrade.
USB-PART-B= ESP boot for USB-PART-A