Page 1 of 1
Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 6:14 am
by scatman98
Hi guys
Using an X1 carbon ThinkPad Gen3 8gb ram 256gb ssd.
As soon as I run an update on fresh install malware gets installed like hydra, squashfs-tools-ng, slack , tiger-otheros, unburden-home-dir , vagrant-sshsfs , vagrant-libvirt, vbackup , unionfs-fuse , python3-cinder, python-flufl, ruby-lockfile and many more.
Hacker likely somewhere in neighbourhood.maybe next door.
Before I can add a vpn the system runs an update and I get the same malware
Also for using dns over tls I need to run a sudo apt update and get in the same situation.
I'm attaching a pic for you to look at of the live log at install (usb is encrypted) and provide some feedback
Regards
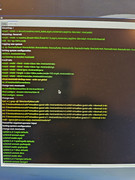
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 6:22 am
by Eadwine Rose
Please don't post screenshots of code output, they cannot be searched. You can post code on the forum like this:
[code]code output here[/code]
Also with all requests, as per forum rules (which, if you haven't, please read), please share your full Quick System Info, do not edit.
If need be, you can do this using the LiveUSB, thanks.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 7:06 am
by j2mcgreg
You need to post the output from the QSI utility. The Quick System Info (QSI) utility is located in MX Tools and its output is automatically formatted for use here in the forum. Run the QSI utility, click “Copy for Forum” at the bottom and then just paste it here in your thread.
Forum Rules
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 7:26 am
by Nokkaelaein
What you are listing is not malware; they are just "regular" software packages, tools for different purposes. Why they get installed seemingly automatically on your system is something that will hopefully be cleared below, but a
hacker next door causing this seems to be on the unlikely side of the possible causes here

Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 7:50 am
by scatman98
these are the programs installed on simply running sudo for the first time
Code: Select all
apt search 'nfs-*'
Sorting... Done
Full Text Search... Done
4pane/stable 8.0-1+b2 amd64
four-pane detailed-list file manager
arch-install-scripts/stable,stable 28-1 all
scripts aimed at automating some menial tasks
backuppc/stable 4.4.0-8 amd64
high-performance, enterprise-grade system for backing up PCs
cinder-api/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - API server
cinder-backup/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - Backup server
cinder-common/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - common files
cinder-doc/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - doc
cinder-scheduler/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - Scheduler server
cinder-volume/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - Volume server
collectd-core/stable 5.12.0-14 amd64
statistics collection and monitoring daemon (core system)
collectl/stable,stable 4.3.1-1 all
Utility to collect Linux performance data
diod/stable 1.0.24-5 amd64
I/O forwarding server for 9P
dracut-core/stable 059-4 amd64
dracut is an event driven initramfs infrastructure (core tools)
dracut-network/stable,stable 059-4 all
dracut is an event driven initramfs infrastructure (network modules)
dsniff/stable 2.4b1+debian-31 amd64
Various tools to sniff network traffic for cleartext insecurities
fai-nfsroot/stable,stable 6.0.3+deb12u1 all
Fully Automatic Installation nfsroot package
gfarm-client/stable 2.7.20+dfsg-1+b2 amd64
Gfarm file system clients
gfarm-doc/stable,stable 2.7.20+dfsg-1 all
Gfarm file system documentation
gfarm2fs/stable 1.2.16-1 amd64
FUSE program to mount the Gfarm file system
gfmd/stable 2.7.20+dfsg-1+b2 amd64
Gfarm file system metadata server
gfsd/stable 2.7.20+dfsg-1+b2 amd64
Gfarm file system daemon
gnome-system-tools/stable 3.0.0-9.1 amd64
Cross-platform configuration utilities
golang-github-d-tux-go-fstab-dev/stable,stable 0.0.0+git.2014.12.04.eb4090f265-3 all
simple fstab parser
golang-github-hanwen-go-fuse-dev/stable,stable 2.1.0+git20220822.58a7e14-1 all
Native Go bindings for the FUSE kernel module
hydra/stable 9.4-1 amd64
very fast network logon cracker
hydra-gtk/stable 9.4-1 amd64
very fast network logon cracker - GTK+ based GUI
jftp/stable,stable 1.60+dfsg-4 all
Java GUI client for FTP, SMB, SFTP and NFS
kdenetwork-filesharing/stable 4:22.12.3-1 amd64
network filesharing configuration module
kio/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction
libfile-fcntllock-perl/stable 0.22-4+b1 amd64
Perl module for file locking with fcntl(2)
libfile-nfslock-perl/stable,stable 1.29-2 all
perl module to do NFS (or not) locking
libfst-dev/stable 1.7.9-5 amd64
weighted finite-state transducers library (development)
libfst-tools/stable 1.7.9-5 amd64
weighted finite-state transducers library (tools)
libfst22/stable 1.7.9-5 amd64
weighted finite-state transducers library (runtime)
libfst22-plugins-base/stable 1.7.9-5 amd64
weighted finite-state transducers library (base plugins)
libgfarm-dev/stable 2.7.20+dfsg-1+b2 amd64
Gfarm file system development files
libgfarm1/stable 2.7.20+dfsg-1+b2 amd64
Gfarm file system runtime library
libio-aio-perl/stable 4.80-1 amd64
asynchronous IO module for Perl
libkf5kio-dev/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (development files)
libkf5kio-doc/stable,stable 5.103.0-1+deb12u1 all
resource and network access abstraction (documentation)
libkf5kiocore5/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (KIO core library)
libkf5kiofilewidgets5/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (KIO file widgets library)
libkf5kiogui5/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (KIO gui library)
libkf5kiontlm5/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (KIO NTLM library)
libkf5kiowidgets5/stable 5.103.0-1+deb12u1 amd64
resource and network access abstraction (KIO widgets library)
liblockfile1/stable,now 1.17-1+b1 amd64 [installed,automatic]
NFS-safe locking library
libnfs-dev/stable 4.0.0-1 amd64
NFS client library (development files)
libnfs-utils/stable 4.0.0-1 amd64
NFS client library (binaries)
libnfs13/stable,now 4.0.0-1 amd64 [installed,automatic]
NFS client library (shared library)
libnfsidmap-dev/stable 1:2.6.2-4+deb12u1 amd64
header files and docs for libnfsidmap
libnfsidmap1/stable 1:2.6.2-4+deb12u1 amd64 [upgradable from: 1:2.6.2-4]
NFS idmapping library
libntirpc-dev/stable 4.3-2 amd64
new transport-independent RPC library - development files
libntirpc4.3/stable 4.3-2 amd64
new transport-independent RPC library
libsquashfs-dev/stable 1.2.0-1 amd64
New set of tools for working with SquashFS images - development
libsquashfs1/stable 1.2.0-1 amd64
New set of tools for working with SquashFS images - shared library
libsys-gamin-perl/stable 0.1-3+b1 amd64
Perl interface to Gamin (File Access Monitor implementation)
libtirpc-common/stable,stable,now 1.3.3+ds-1 all [installed]
transport-independent RPC library - common files
libtirpc-dev/stable,now 1.3.3+ds-1 amd64 [installed,automatic]
transport-independent RPC library - development files
libtirpc3/stable,now 1.3.3+ds-1 amd64 [installed]
transport-independent RPC library
libuutil3linux/stable 2.1.11-1+deb12u1 amd64
Solaris userland utility library for Linux
libyanfs-java/stable,stable 0.0+cvs20070825-4.1 all
Yet Another NFS - a Java NFS library
manpages/stable,stable,now 6.03-2 all [installed]
Manual pages about using a GNU/Linux system
manpages-cs/stable,stable 4.18.1-1 all
Czech man pages
manpages-da/stable,stable 4.18.1-1 all
Danish man pages
manpages-de/stable,stable 4.18.1-1 all
German man pages
manpages-es/stable,stable 4.18.1-1 all
Spanish man pages
manpages-fr/stable,stable 4.18.1-1 all
French man pages
manpages-hu/stable,stable 1:4.18.1-1 all
Hungarian man pages
manpages-it/stable,stable 4.18.1-1 all
Italian man pages
manpages-nl/stable,stable 4.18.1-1 all
Dutch man pages
manpages-pl/stable,stable 1:4.18.1-1 all
Polish man pages
manpages-pt-br/stable,stable 4.18.1-1 all
Brazilian Portuguese man pages
manpages-ru/stable,stable 4.18.1-1 all
Russian man pages
manpages-tr/stable,stable 2.0.6-2 all
Turkish version of the manual pages
mb2md/stable,stable 3.20-10 all
Convert Mbox mailboxes to Maildir format
mergerfs/stable 2.33.5-1 amd64
another FUSE union filesystem
mhddfs/stable 0.1.39+nmu2 amd64
file system for unifying several mount points into one
monitoring-plugins-contrib/stable 42.20230308+deb12u1+b1 amd64
Plugins for nagios compatible monitoring systems
nbd-client/stable 1:3.24-1.1 amd64
Network Block Device protocol - client
nbd-server/stable 1:3.24-1.1 amd64
Network Block Device protocol - server
nfs-common/stable 1:2.6.2-4+deb12u1 amd64 [upgradable from: 1:2.6.2-4]
NFS support files common to client and server
nfs-common-modified-init/mx,mx,now 19.07.01 all [installed]
modified nfs-common init script for mx and antiX linux
nfs-ganesha/stable 4.3-2 amd64
NFS server in User Space
nfs-ganesha-ceph/stable 4.3-2 amd64
nfs-ganesha fsal ceph libraries
nfs-ganesha-doc/stable,stable 4.3-2 all
Documentation for nfs-ganesha
nfs-ganesha-gluster/stable 4.3-2 amd64
nfs-ganesha fsal gluster libraries
nfs-ganesha-gpfs/stable 4.3-2 amd64
nfs-ganesha fsal gpfs libraries
nfs-ganesha-mem/stable 4.3-2 amd64
nfs-ganesha fsal mem libraries
nfs-ganesha-mount-9p/stable,stable 4.3-2 all
nfs-ganesha mount.9P
nfs-ganesha-nullfs/stable 4.3-2 amd64
nfs-ganesha fsal nullfs libraries
nfs-ganesha-proxy-v4/stable 4.3-2 amd64
nfs-ganesha fsal proxy v4 libraries
nfs-ganesha-rados-grace/stable 4.3-2 amd64
nfs-ganesha ganesha-rados-grace program
nfs-ganesha-rgw/stable 4.3-2 amd64
nfs-ganesha fsal rgw libraries
nfs-ganesha-vfs/stable 4.3-2 amd64
nfs-ganesha fsal vfs libraries
nfs-kernel-server/stable 1:2.6.2-4+deb12u1 amd64 [upgradable from: 1:2.6.2-4]
support for NFS kernel server
nfs4-acl-tools/stable 0.3.7-1 amd64
Commandline and GUI ACL utilities for the NFSv4 client
nfstrace/stable 0.4.3.2+git20200805+b220d04-2.2 amd64
NFS tracing/monitoring/capturing/analyzing tool
nfstrace-doc/stable,stable 0.4.3.2+git20200805+b220d04-2.2 all
NFS tracing/monitoring/capturing/analyzing tool (documentation)
nfswatch/stable 4.99.12-1 amd64
Program to monitor NFS traffic for the console
nmon/stable 16n+debian-1+b1 amd64
performance monitoring tool for Linux
portsentry/stable 1.2-14+b1 amd64
Portscan detection daemon
python-flufl.lock-doc/stable,stable 5.0.1-4 all
NFS-safe file-based lock with timeouts (common documentation)
python-tackerclient-doc/stable,stable 1.12.0-2 all
CLI and Client Library for OpenStack Tacker - doc
python3-cinder/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - Python libraries
python3-flufl.lock/stable,stable 5.0.1-4 all
NFS-safe file-based lock with timeouts (Python 3)
python3-nfs-ganesha/stable,stable 4.3-2 all
Python bindings for nfs-ganesha
python3-tackerclient/stable,stable 1.12.0-2 all
CLI and Client Library for OpenStack Tacker - Python 3.x
quota/stable 4.06-1+b2 amd64
disk quota management tools
resource-agents/stable 1:4.12.0-2 amd64
Cluster Resource Agents
ruby-lockfile/stable,stable 2.1.3-1.1 all
create NFS-safe lockfiles
ruby-spring-watcher-listen/stable,stable 2.0.1-1.1 all
Makes spring watch files using the listen library
slack/stable,stable 1:0.15.2-11 all
configuration management program for lazy admins
squashfs-tools-ng/stable 1.2.0-1 amd64
New set of tools for working with SquashFS images
tcpdump/stable 4.99.3-1 amd64
command-line network traffic analyzer
texlive-latex-base/stable,stable 2022.20230122-3 all
TeX Live: LaTeX fundamental packages
texlive-latex-extra/stable,stable 2022.20230122-4 all
TeX Live: LaTeX additional packages
texlive-luatex/stable,stable 2022.20230122-3 all
TeX Live: LuaTeX packages
texlive-plain-generic/stable,stable 2022.20230122-4 all
TeX Live: Plain (La)TeX packages
tiger-otheros/stable 1:3.2.4~rc1-3.2 amd64
security auditing and intrusion detection scripts for Unix based systems
udpcast/stable 20120424-2+b1 amd64
multicast file transfer tool
unburden-home-dir/stable,stable 0.4.2 all
Remove or move cache files automatically from user's home
unionfs-fuse/stable 1.0-1+b1 amd64
Fuse implementation of unionfs
vagrant-libvirt/stable,stable 0.11.2-1 all
Vagrant plugin that adds an Libvirt provider to Vagrant
vagrant-sshfs/stable,stable 1.3.7-1 all
vagrant plugin that adds synced folder support with sshfs
vbackup/stable,stable 1.0.1-1.1 all
modular backup utility
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 7:51 am
by scatman98
This is the QSI
Code: Select all
Snapshot created on: 20241215_1628
System:
Kernel: 6.1.0-28-amd64 [6.1.119-1] arch: x86_64 bits: 64 compiler: gcc v: 12.2.0
parameters: BOOT_IMAGE=/boot/vmlinuz-6.1.0-28-amd64 root=UUID=<filter> ro quiet splash
init=/lib/systemd/systemd
Desktop: Xfce v: 4.18.1 tk: Gtk v: 3.24.36 info: xfce4-panel wm: xfwm v: 4.18.0 vt: 7
dm: LightDM v: 1.26.0 Distro: MX-23.4_x64 Libretto December 15 2024 base: Debian GNU/Linux 12
(bookworm)
Machine:
Type: Laptop System: LENOVO product: 20BTS0HJ10 v: ThinkPad X1 Carbon 3rd
serial: <superuser required> Chassis: type: 10 serial: <superuser required>
Mobo: LENOVO model: 20BTS0HJ10 v: SDK0E50510 WIN serial: <superuser required> UEFI: LENOVO
v: N14ET56W (1.34 ) date: 08/31/2021
Battery:
ID-1: BAT0 charge: 27.7 Wh (99.3%) condition: 27.9/50.0 Wh (55.9%) volts: 17.0 min: 15.0
model: LGC 45N1707 type: Li-poly serial: <filter> status: not charging
CPU:
Info: model: Intel Core i7-5600U bits: 64 type: MT MCP arch: Broadwell gen: core 5 level: v3
note: check built: 2015-18 process: Intel 14nm family: 6 model-id: 0x3D (61) stepping: 4
microcode: 0x2F
Topology: cpus: 1x cores: 2 tpc: 2 threads: 4 smt: enabled cache: L1: 128 KiB
desc: d-2x32 KiB; i-2x32 KiB L2: 512 KiB desc: 2x256 KiB L3: 4 MiB desc: 1x4 MiB
Speed (MHz): avg: 843 high: 899 min/max: 500/3200 scaling: driver: intel_cpufreq
governor: ondemand cores: 1: 899 2: 817 3: 851 4: 807 bogomips: 20750
Flags: avx avx2 ht lm nx pae sse sse2 sse3 sse4_1 sse4_2 ssse3 vmx
Vulnerabilities:
Type: gather_data_sampling status: Not affected
Type: itlb_multihit status: KVM: VMX disabled
Type: l1tf mitigation: PTE Inversion; VMX: conditional cache flushes, SMT vulnerable
Type: mds mitigation: Clear CPU buffers; SMT vulnerable
Type: meltdown mitigation: PTI
Type: mmio_stale_data status: Unknown: No mitigations
Type: reg_file_data_sampling status: Not affected
Type: retbleed status: Not affected
Type: spec_rstack_overflow status: Not affected
Type: spec_store_bypass mitigation: Speculative Store Bypass disabled via prctl
Type: spectre_v1 mitigation: usercopy/swapgs barriers and __user pointer sanitization
Type: spectre_v2 mitigation: Retpolines; IBPB: conditional; IBRS_FW; STIBP: conditional; RSB
filling; PBRSB-eIBRS: Not affected; BHI: Not affected
Type: srbds mitigation: Microcode
Type: tsx_async_abort mitigation: Clear CPU buffers; SMT vulnerable
Graphics:
Device-1: Intel HD Graphics 5500 vendor: Lenovo driver: i915 v: kernel arch: Gen-8
process: Intel 14nm built: 2014-15 ports: active: eDP-1 empty: DP-1, DP-2, HDMI-A-1, HDMI-A-2
bus-ID: 00:02.0 chip-ID: 8086:1616 class-ID: 0300
Display: x11 server: X.Org v: 1.21.1.7 compositor: xfwm v: 4.18.0 driver: X:
loaded: modesetting unloaded: fbdev,vesa dri: iris gpu: i915 display-ID: :0.0 screens: 1
Screen-1: 0 s-res: 2560x1440 s-dpi: 96 s-size: 677x381mm (26.65x15.00") s-diag: 777mm (30.58")
Monitor-1: eDP-1 model: LG Display 0x0419 built: 2013 res: 2560x1440 hz: 60 dpi: 210 gamma: 1.2
size: 310x174mm (12.2x6.85") diag: 355mm (14") ratio: 16:9 modes: 2560x1440
API: OpenGL v: 4.6 Mesa 22.3.6 renderer: Mesa Intel HD Graphics 5500 (BDW GT2)
direct-render: Yes
Audio:
Device-1: Intel Broadwell-U Audio vendor: Lenovo driver: snd_hda_intel v: kernel bus-ID: 00:03.0
chip-ID: 8086:160c class-ID: 0403
Device-2: Intel Wildcat Point-LP High Definition Audio vendor: Lenovo driver: snd_hda_intel
v: kernel bus-ID: 00:1b.0 chip-ID: 8086:9ca0 class-ID: 0403
API: ALSA v: k6.1.0-28-amd64 status: kernel-api tools: alsamixer,amixer
Server-1: PipeWire v: 1.0.0 status: active with: 1: pipewire-pulse status: active
2: wireplumber status: active 3: pipewire-alsa type: plugin 4: pw-jack type: plugin
tools: pactl,pw-cat,pw-cli,wpctl
Network:
Device-1: Intel Ethernet I218-LM vendor: Lenovo driver: e1000e v: kernel port: 3080
bus-ID: 00:19.0 chip-ID: 8086:15a2 class-ID: 0200
IF: eth0 state: down mac: <filter>
IF-ID-1: eth1 state: unknown speed: -1 duplex: half mac: <filter>
Bluetooth:
Device-1: Samsung Galaxy series misc. (tethering mode) type: USB driver: rndis_host v: kernel
bus-ID: 1-1:3 chip-ID: 04e8:6863 class-ID: 0a00 serial: <filter>
Drives:
Local Storage: total: 238.47 GiB used: 9 GiB (3.8%)
SMART Message: Unable to run smartctl. Root privileges required.
ID-1: /dev/sda maj-min: 8:0 vendor: Samsung model: MZNTE256HMHP-000L7 size: 238.47 GiB
block-size: physical: 512 B logical: 512 B speed: 6.0 Gb/s type: SSD serial: <filter> rev: 9L6Q
scheme: GPT
Partition:
ID-1: / raw-size: 12.62 GiB size: 12.32 GiB (97.63%) used: 9 GiB (73.0%) fs: ext4 dev: /dev/sda1
maj-min: 8:1
ID-2: /boot/efi raw-size: 677 MiB size: 675.6 MiB (99.80%) used: 288 KiB (0.0%) fs: vfat
dev: /dev/sda3 maj-min: 8:3
Swap:
Kernel: swappiness: 15 (default 60) cache-pressure: 100 (default)
ID-1: swap-1 type: file size: 2 GiB used: 0 KiB (0.0%) priority: -2 file: /swap/swap
Sensors:
System Temperatures: cpu: 42.0 C pch: 39.0 C mobo: N/A
Fan Speeds (RPM): fan-1: 0
Repos:
Packages: pm: dpkg pkgs: 2117 libs: 1052 tools: apt,apt-get,aptitude,nala,synaptic pm: rpm
pkgs: 0 pm: flatpak pkgs: 0
No active apt repos in: /etc/apt/sources.list
Active apt repos in: /etc/apt/sources.list.d/debian-stable-updates.list
1: deb http://deb.debian.org/debian bookworm-updates main contrib non-free non-free-firmware
Active apt repos in: /etc/apt/sources.list.d/debian.list
1: deb http://deb.debian.org/debian bookworm main contrib non-free non-free-firmware
2: deb http://security.debian.org/debian-security bookworm-security main contrib non-free non-free-firmware
Active apt repos in: /etc/apt/sources.list.d/mx.list
1: deb https://mirror.kku.ac.th/mx-packages/mx/repo/ bookworm main non-free
Info:
Processes: 230 Uptime: 19m wakeups: 1 Memory: 7.64 GiB used: 3.13 GiB (40.9%) Init: systemd
v: 252 target: graphical (5) default: graphical tool: systemctl Compilers: gcc: 12.2.0 alt: 12
Client: shell wrapper v: 5.2.15-release inxi: 3.3.26
Boot Mode: UEFI
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 7:58 am
by scatman98
Nokkaelaein wrote: Mon Jan 13, 2025 7:26 am
What you are listing is not malware; they are just "regular" software packages, tools for different purposes. Why they get installed seemingly automatically on your system is something that will hopefully be cleared below, but a
hacker next door causing this seems to be on the unlikely side of the possible causes here

it says cracker in the description , i think cracker is malware, has no business to be on a new os install!
Code: Select all
hydra-gtk/stable 9.4-1 amd64 very fast network logon cracker - GTK+ based GUI[/code[]]
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:07 am
by Nokkaelaein
scatman98 wrote: Mon Jan 13, 2025 7:58 am
it says cracker in the description , i think cracker is malware, has no business to be on a new os install!
No, it's not malware, it's a security tool developed for breaching login passwords. Why it is installed on your system is hopefully discovered later in this thread. Similarly, your listed other software packages are just that, software packages for various different purposes (readily available in official repositories).
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:21 am
by scatman98
Nokkaelaein wrote: Mon Jan 13, 2025 8:07 am
scatman98 wrote: Mon Jan 13, 2025 7:58 am
it says cracker in the description , i think cracker is malware, has no business to be on a new os install!
No, it's not malware, it's a security tool developed for breaching login passwords. Why it is installed on your system is hopefully discovered later in this thread. Similarly, your listed other software packages are just that, software packages for various different purposes (readily available in official repositories).
i did spot some in the repos, but they don't show as installed in the GUI of mx- installer. Image attached.
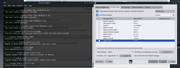
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:23 am
by Nokkaelaein
That's because they are not installed. Checked your used command more closely, and you are doing an "apt search" - this searches for all suitable available packages, not merely packages that are installed.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:31 am
by scatman98
Nokkaelaein wrote: Mon Jan 13, 2025 8:23 am
That's because they are not installed. Checked your used command more closely, and you are doing an "apt search" - this searches for all suitable available packages, not merely packages that are installed.
Thanks for the info, so this searchable items list is getting populated by available programs when sudo command is run initially is the idea here ?
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:35 am
by Nokkaelaein
scatman98 wrote: Mon Jan 13, 2025 8:31 am
Thanks for the info, so this searchable items list is getting populated by available programs when sudo command is run initially is the idea here ?
No, sudo doesn't have anything to do with it. Sudo is a utility in unix/linux/etc. to run things with elevated privileges, and it only does that. It's most often used in admin tasks a regular user account doesn't have sufficient privileges for. In turn, apt just has a command called "search" that lists available packages matching the search string, and that's it. You can do an apt search with standard user privileges, too, with no use of sudo. (Provided that a system has fetched the package lists for the repositories in use - manually fetching the lists is done for example by running "apt update", and this
is an action that requires elevated privileges. Anyway, everything seems to be okay with your system

)
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:42 am
by siamhie
scatman98 wrote: Mon Jan 13, 2025 6:14 am
As soon as I run an update on fresh install malware gets installed like hydra, squashfs-tools-ng, slack , tiger-otheros, unburden-home-dir , vagrant-sshsfs , vagrant-libvirt, vbackup , unionfs-fuse , python3-cinder, python-flufl, ruby-lockfile and many more.
Not one of these programs are installed on my system I installed just over a week ago.
Check again.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:43 am
by DukeComposed
Nokkaelaein wrote: Mon Jan 13, 2025 8:07 am
No, it's not malware, it's a security tool developed for breaching login passwords. Why it is installed on your system is hopefully discovered later in this thread.
Agreed, network security tools are an important part of the Linux ecosystem. We also don't know for sure that any of these packages are actually installed, since "apt search <something>" can list a bunch of software, but it doesn't actually install any of it. dpkg -l | grep hydra will be useful here in showing if any of these tools are actually present on the system.
Code: Select all
Repos:
Packages: pm: dpkg pkgs: 2117 libs: 1052 tools: apt,apt-get,aptitude,nala,synaptic
QSI shows there are 2,117 packages installed on the system currently. I loaded an MX 23.4 x64 ISO to match the OS in the QSI and it shows 2,114 packages present in the live session. I honestly don't think any of these NFS-related applications are getting installed.
Perhaps OP thinks that "apt search <something>" searches the local system for installed software, rather than what "apt search" really does: searches the repositories configured on the system for
available packages.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:44 am
by Nokkaelaein
DukeComposed wrote: Mon Jan 13, 2025 8:43 am
We also don't know for sure that any of these packages are actually installed, since "apt search <something>" can list a bunch of software, but it doesn't actually install any of it.
Indeed, ninja'd above while you were writing this, heh :)
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:58 am
by scatman98
DukeComposed wrote: Mon Jan 13, 2025 8:43 am
Nokkaelaein wrote: Mon Jan 13, 2025 8:07 am
No, it's not malware, it's a security tool developed for breaching login passwords. Why it is installed on your system is hopefully discovered later in this thread.
Agreed, network security tools are an important part of the Linux ecosystem. We also don't know for sure that any of these packages are actually installed, since "apt search <something>" can list a bunch of software, but it doesn't actually install any of it. dpkg -l | grep hydra will be useful here in showing if any of these tools are actually present on the system.
Code: Select all
Repos:
Packages: pm: dpkg pkgs: 2117 libs: 1052 tools: apt,apt-get,aptitude,nala,synaptic
QSI shows there are 2,117 packages installed on the system currently. I loaded an MX 23.4 x64 ISO to match the OS in the QSI and it shows 2,114 packages present in the live session. I honestly don't think any of these NFS-related applications are getting installed.
Perhaps OP thinks that "apt search <something>" searches the local system for installed software, rather than what "apt search" really does: searches the repositories configured on the system for
available packages.
yes i did assume these were installed packages

i dont understand though why does 'apt search' query show more than just the results from ' dpkg -l | grep' only after sudo is run inititially otherwise there is no difference in results when i search for 'apt search 'nfs-*' or dpkg -l | grep 'nfs-*'
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 9:05 am
by Nokkaelaein
scatman98 wrote: Mon Jan 13, 2025 8:58 am
i dont understand though why does 'apt search' query show more than just the results from ' dpkg -l | grep' only after sudo is run inititially otherwise there is no difference in results when i search for 'apt search 'nfs-*' or dpkg -l | grep 'nfs-*'
Again, sudo doesn't have an effect on this. It's
what you run with elevated privileges using sudo. If your system doesn't have the package lists fetched, apt search will not show you those available packages in the repos that aren't installed. I guarantee the situation will not change if you just run sudo by itself. If, in a situation where there are no package lists on your local machine, you use sudo to run a command (that requires elevated privileges) that fetches them, then the situation changes, and "apt search" shows you all available packages, including ones that aren't installed on your system.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 9:14 am
by DukeComposed
scatman98 wrote: Mon Jan 13, 2025 8:58 am
i dont understand though why does 'apt search' query show more than just the results from ' dpkg -l | grep' only after sudo is run inititially otherwise there is no difference in results when i search for 'apt search 'nfs-*' or dpkg -l | grep 'nfs-*'
The cache gets updated. "man apt" and "man apt-cache" might be useful here in describing how these tools work, particularly the section that goes:
Code: Select all
apt-cache does not manipulate the state of the system but does provide operations to search and generate interesting output from the package metadata. The metadata is acquired and updated via the 'update' command of e.g. apt-get, so that it can be outdated if the last update is too long ago, but in exchange apt-cache works independently of the availability of the configured sources (e.g. offline).
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 9:20 am
by scatman98
Nokkaelaein wrote: Mon Jan 13, 2025 9:05 am
scatman98 wrote: Mon Jan 13, 2025 8:58 am
i dont understand though why does 'apt search' query show more than just the results from ' dpkg -l | grep' only after sudo is run inititially otherwise there is no difference in results when i search for 'apt search 'nfs-*' or dpkg -l | grep 'nfs-*'
Again, sudo doesn't have an effect on this. It's
what you run with elevated privileges using sudo. If your system doesn't have the package lists fetched, apt search will not show you those available packages in the repos that aren't installed. I guarantee the situation will not change if you just run sudo by itself. If, in a situation where there are no package lists on your local machine, you use sudo to run a command (that requires elevated privileges) that fetches them, then the situation changes, and "apt search" shows you all available packages, including ones that aren't installed on your system.
i had run three commands with sudo all were "command not found" . these are the commands i had run to move from few to many results with apt search, does this check out as legit behaviour?
Code: Select all
psa@mx:~
$ apt search 'nfs-*'
Sorting... Done
Full Text Search... Done
liblockfile1/now 1.17-1+b1 amd64 [installed,local]
NFS-safe locking library
libnfs13/now 4.0.0-1 amd64 [installed,local]
NFS client library (shared library)
libnfsidmap1/now 1:2.6.2-4 amd64 [installed,local]
NFS idmapping library
libtirpc-common/now 1.3.3+ds-1 all [installed,local]
transport-independent RPC library - common files
libtirpc-dev/now 1.3.3+ds-1 amd64 [installed,local]
transport-independent RPC library - development files
libtirpc3/now 1.3.3+ds-1 amd64 [installed,local]
transport-independent RPC library
manpages/now 6.03-2 all [installed,local]
Manual pages about using a GNU/Linux system
nfs-common/now 1:2.6.2-4 amd64 [installed,local]
NFS support files common to client and server
nfs-common-modified-init/now 19.07.01 all [installed,local]
modified nfs-common init script for mx and antiX linux
nfs-kernel-server/now 1:2.6.2-4 amd64 [installed,local]
support for NFS kernel server
psa@mx:~
$ sudo /etc/init.d/nscd restart
[sudo] password for psa:
sudo: /etc/init.d/nscd: command not found
psa@mx:~
$ sudo /etc/init.d/dnsmasq restart
sudo: /etc/init.d/dnsmasq: command not found
psa@mx:~
$ sudo /etc/init.d/named restart
sudo: /etc/init.d/named: command not found
psa@mx:~
$ apt search 'nfs-*'
Sorting... Done
Full Text Search... Done
4pane/stable 8.0-1+b2 amd64
four-pane detailed-list file manager
arch-install-scripts/stable,stable 28-1 all
scripts aimed at automating some menial tasks
backuppc/stable 4.4.0-8 amd64
high-performance, enterprise-grade system for backing up PCs
cinder-api/stable,stable,stable-security,stable-security 2:21.3.1-1~deb12u1 all
OpenStack block storage system - API server
.................
.................
.....................
....................
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 9:26 am
by siamhie
What are you searching for?
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 9:51 am
by scatman98
siamhie wrote: Mon Jan 13, 2025 9:26 am
What are you searching for?
The distro is locking me out of internet access, login access to desktop, folder/file access , and sometimes fixing itself randomly so i'm looking to fix this behaviour.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:06 am
by Eadwine Rose
Does this similar behavior also happen on the LiveUSB?
How have you installed things on your system?
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:09 am
by scatman98
Eadwine Rose wrote: Mon Jan 13, 2025 10:06 am
Does this similar behavior also happen on the LiveUSB?
How have you installed things on your system?
edit: I had this happen especially with the writable usb option i think the usb drive was corrupted while running live? only tried with non writable option after that and yes same behavior.
clean install.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:12 am
by Eadwine Rose
I was thinking more of the software ON the system.
Did you use the recommended method MXPI, or did you use deb downloads, stuff like that?
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:25 am
by scatman98
Eadwine Rose wrote: Mon Jan 13, 2025 10:12 am
I was thinking more of the software ON the system.
Did you use the recommended method MXPI, or did you use deb downloads, stuff like that?
i downloaded using mxpi
when i run sudo for one program only in terminal, say, nordvpn client, it auto updates all repos and i get the same behaviour.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:43 am
by Eadwine Rose
Nokkaelaein wrote: Mon Jan 13, 2025 7:26 am
What you are listing is not malware; they are just "regular" software packages, tools for different purposes. Why they get installed seemingly automatically on your system is something that will hopefully be cleared below, but a
hacker next door causing this seems to be on the unlikely side of the possible causes here

Likely indeed just dependencies of things that were intended to install.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 10:46 am
by siamhie
scatman98 wrote: Mon Jan 13, 2025 10:25 am
Eadwine Rose wrote: Mon Jan 13, 2025 10:12 am
I was thinking more of the software ON the system.
Did you use the recommended method MXPI, or did you use deb downloads, stuff like that?
i downloaded using mxpi
when i run sudo for one program only in terminal, say, nordvpn client, it auto updates all repos and i get the same behaviour.
Why are you running the nord client as sudo? Run it as a user. These are the commands I use.
The first one is to just connect quickly. The second is when I'm torrenting.
The third is when I want to use a double vpn connection. The last is to disconnect.
Code: Select all
nordvpn connect
nordvpn connect P2P
nordvpn connect double_vpn
nordvpn disconnect
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 11:06 am
by Nokkaelaein
Eadwine Rose wrote: Mon Jan 13, 2025 10:43 am
Likely indeed just dependencies of things that were intended to install.
Ah no, that was about the results of "apt search", and a misunderstanding of what the command is used for (i.e. listing
all available packages fitting the search, instead of showing packages somehow related to the software on the local system).
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 11:16 am
by Eadwine Rose
I'd say: if you are scared of having been hacked, or basically, if you did something which you have no idea of what you did, and your system is not behaving, start over, and install from MXPI only.
In the time it takes to go on a chase, because I still really don't understand what you want or what is going on, you could be up and running properly again.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 12:28 pm
by Stevo
Captain America was pretty good at fighting Hydra...
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 12:47 pm
by scatman98
siamhie wrote: Mon Jan 13, 2025 10:46 am
scatman98 wrote: Mon Jan 13, 2025 10:25 am
Eadwine Rose wrote: Mon Jan 13, 2025 10:12 am
I was thinking more of the software ON the system.
Did you use the recommended method MXPI, or did you use deb downloads, stuff like that?
i downloaded using mxpi
when i run sudo for one program only in terminal, say, nordvpn client, it auto updates all repos and i get the same behaviour.
Why are you running the nord client as sudo? Run it as a user. These are the commands I use.
The first one is to just connect quickly. The second is when I'm torrenting.
The third is when I want to use a double vpn connection. The last is to disconnect.
Code: Select all
nordvpn connect
nordvpn connect P2P
nordvpn connect double_vpn
nordvpn disconnect
to install the client i was using the command on the website which brought up all the updates
Code: Select all
sh <(curl -sSf https://downloads.nordcdn.com/apps/linux/install.sh)
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 12:56 pm
by scatman98
Eadwine Rose wrote: Mon Jan 13, 2025 11:16 am
I'd say: if you are scared of having been hacked, or basically, if you did something which you have no idea of what you did, and your system is not behaving, start over, and install from MXPI only.
In the time it takes to go on a chase, because I still really don't understand what you want or what is going on, you could be up and running properly again.
MXPI is the mx-packageinstaller right? i was using that.
i'm using deb files for now and skipping mxpi since it initiates all the repo updates which causes the same sort of behaviour to re appear.
i think if i could get dns over tls working without connecting to the internet first on a clean install that might help. i need to download systemd-resolved before i can get secure dns working. if this came pre-installed in the iso that would help with a secure connection to the internet and rule out DNS cache poisoning as one possibility of issues with MXPI.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 1:08 pm
by j2mcgreg
I'm going to suggest that maybe your main repository is malfunctioning and that you should use Repo Manager in MX Tools to switch to one of these four which are owned and operated by the MX team:
Alblasserdam, The Netherlands
Los Angeles, California, U.S.A.
Salt Lake City, Utah, U.S.A.
Milan, Italy
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 1:26 pm
by scatman98
j2mcgreg wrote: Mon Jan 13, 2025 1:08 pm
I'm going to suggest that maybe your main repository is malfunctioning and that you should use Repo Manager in MX Tools to switch to one of these four which are owned and operated by the MX team:
Alblasserdam, The Netherlands
Los Angeles, California, U.S.A.
Salt Lake City, Utah, U.S.A.
Milan, Italy
i'm on mxrepo.com i need a secure connection to the repo. its a clean install so the malfunction is only possible from some redirection of traffic etween the router and isp via a mitm attack on dns cache.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 4:08 pm
by uncle mark
scatman98 wrote: Mon Jan 13, 2025 1:26 pm
i'm on mxrepo.com i need a secure connection to the repo. its a clean install so the malfunction is only possible from some redirection of traffic etween the router and isp via a mitm attack on dns cache.
Stop with the "hacked" and "redirection" and "mitm" nonsense. Post your QSI and let the community see what your system is doing. You've buggered it up somehow and either need to straighten it out (probably a repo issue) or start all over.
MX is rock solid and secure out of the box. Get your system installed and fleshed out, and then ask for advise on hardening it if you think it's required. Me, I've never found it necessary. I'm not that important.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 5:50 pm
by siamhie
scatman98 wrote: Mon Jan 13, 2025 12:47 pm
to install the client i was using the command on the website which brought up all the updates
Code: Select all
sh <(curl -sSf https://downloads.nordcdn.com/apps/linux/install.sh)
The nordvpn app is in MXPI under the Network section of Popular Applications.
No need to download from the site, it will set everything up for you.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 5:56 pm
by siamhie
j2mcgreg wrote: Mon Jan 13, 2025 1:08 pm
I'm going to suggest that maybe your main repository is malfunctioning and that you should use Repo Manager in MX Tools to switch to one of these four which are owned and operated by the MX team:
Alblasserdam, The Netherlands
Los Angeles, California, U.S.A.
Salt Lake City, Utah, U.S.A.
Milan, Italy
Looking at that mirror they are using (
https://mirror.kku.ac.th/mx-packages/mx/repo/pool/main/), there's several directories dating back to 2022.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 6:23 pm
by m_pav
@uncle mark OP posted his QSI on the first page, #6
@scatman98 So having read through all of this I get the impression Linux on the desktop is a relatively new thing for you, and your understanding of Linux and in particular, the Debian ecosystem along with it's package management needs a bit of tweaking.
I suggest you begin by using as your fisrt port of call our pre-built tools and utilities, then take the time to learn about the CLI stuff by finding a page that gives you a beginners guide. There's plenty around to help you to get to grips with the first level or two of terminal usage.
You say you are having some issues with your system, I see you have your Samsung phone connected via USB in bluetooth tethering mode, so it looks like you're connecting to the internet through your phone. Having tried it in the past, I found this method to be less reliable because it requires the phone first be in good shape, really good shape, and many Android phones are not. Secondly, Linux sometimes loads a less than perfect driver for BT Devices, which, if you were affected by it, would cause the connection to be dodgy leading to a sense of weirdness at times.
Concerning the software (packages) on your machine, it's drop dead easy to get a list of all non-factory packages by simply clicking the Whisker menu button (some call it the start button - yuk!) and type UIP, and that's a capital "i", not a lowercase "l". This will bring up the User Installed Packages app. Click the top button in the app and it will query your machines package status and compare it with the "factory image", then print (to the screen) only the package names that do not exist in the factory image, thereby giving you a list of packages installed over and above the factory image.
Concerning the weirdness on your machine, are you using the built-in trackpad by any chance? I've used Lenovos for many years and I find that some models trackpads are overly sensitive and a finger or part of your hand being too close to it can result in unwanted taps leading to weirdness that makes the machine appear to be "posessed" Have you observed anything that resembles this action by any chance?
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 8:34 pm
by j2mcgreg
siamhie wrote: Mon Jan 13, 2025 5:56 pm
j2mcgreg wrote: Mon Jan 13, 2025 1:08 pm
I'm going to suggest that maybe your main repository is malfunctioning and that you should use Repo Manager in MX Tools to switch to one of these four which are owned and operated by the MX team:
Alblasserdam, The Netherlands
Los Angeles, California, U.S.A.
Salt Lake City, Utah, U.S.A.
Milan, Italy
Looking at that mirror they are using (
https://mirror.kku.ac.th/mx-packages/mx/repo/pool/main/), there's several directories dating back to 2022.
I was thinking more along the lines of the infrastructure hosting the mirror rather than the mirrors actual contents.
Re: Hacked by hydra. At wits end.
Posted: Mon Jan 13, 2025 11:56 pm
by scatman98
m_pav wrote: Mon Jan 13, 2025 6:23 pm
@uncle mark OP posted his QSI on the first page, #6
@scatman98 So having read through all of this I get the impression Linux on the desktop is a relatively new thing for you, and your understanding of Linux and in particular, the Debian ecosystem along with it's package management needs a bit of tweaking.
I suggest you begin by using as your fisrt port of call our pre-built tools and utilities, then take the time to learn about the CLI stuff by finding a page that gives you a beginners guide. There's plenty around to help you to get to grips with the first level or two of terminal usage.
You say you are having some issues with your system, I see you have your Samsung phone connected via USB in bluetooth tethering mode, so it looks like you're connecting to the internet through your phone. Having tried it in the past, I found this method to be less reliable because it requires the phone first be in good shape, really good shape, and many Android phones are not. Secondly, Linux sometimes loads a less than perfect driver for BT Devices, which, if you were affected by it, would cause the connection to be dodgy leading to a sense of weirdness at times.
Concerning the software (packages) on your machine, it's drop dead easy to get a list of all non-factory packages by simply clicking the Whisker menu button (some call it the start button - yuk!) and type UIP, and that's a capital "i", not a lowercase "l". This will bring up the
User
Installed
Packages app. Click the top button in the app and it will query your machines package status and compare it with the "factory image", then print (to the screen) only the package names that do not exist in the factory image, thereby giving you a list of packages installed over and above the factory image.
Concerning the weirdness on your machine, are you using the built-in trackpad by any chance? I've used Lenovos for many years and I find that some models trackpads are overly sensitive and a finger or part of your hand being too close to it can result in unwanted taps leading to weirdness that makes the machine appear to be "posessed" Have you observed anything that resembles this action by any chance?
I'm using the phone now as a tethering device since i got repeatedly locked out (changed passwords) of my router Asus rt-ax3000 and resetting it was a hassle. The phone is in good shape, except for the cache poisoning of apps via mitm attacks when running updates but that is cleared with the app cache clearing.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 12:03 am
by scatman98
i have the wifi radio disable in the BIOS however the kernel update is installing drivers for it. is this normal?
Code: Select all
Building module:
Cleaning build area...
./dkms-make.sh...........................
Signing module /var/lib/dkms/8812au/5.13.6/build/8812au.ko
Cleaning build area...
8812au.ko:
Running module version sanity check.
- Original module
- No original module exists within this kernel
- Installation
- Installing to /lib/modules/6.1.0-29-amd64/updates/dkms/
depmod...
Sign command: /usr/lib/linux-kbuild-6.1/scripts/sign-file
Signing key: /var/lib/dkms/mok.key
Public certificate (MOK): /var/lib/dkms/mok.pub
Building module:
Cleaning build area...
make -j4 KERNELRELEASE=6.1.0-29-amd64 KVER=6.1.0-29-amd64....
Signing module /var/lib/dkms/broadcom-sta/6.30.223.271/build/wl.ko
Cleaning build area...
wl.ko:
Running module version sanity check.
- Original module
- No original module exists within this kernel
- Installation
- Installing to /lib/modules/6.1.0-29-amd64/updates/dkms/
this is what i came across the web about 8812au.ko
One of the best chipsets that support monitor mode and packet injection for both 5Ghz and 2.4 Ghz frequencies is the RealTek RTL8812AU, this makes adapters with chipset ideal for hacking, the only problem is this chipset is not natively supported by Kali Linux, therefore we need to install its drivers first before
previously while using wired internet from a different isp, i also found linux kernel 6.10 installed on the system which i had never installed. it did not show up in package managers but did show up while trying to update the live kernel.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 12:23 am
by DukeComposed
scatman98 wrote: Mon Jan 13, 2025 11:56 pm
good shape, except for the cache poisoning of apps via mitm attacks when running updates
You keep using that word. I do not think it means what you think it means.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 1:35 am
by siamhie
scatman98 wrote: Tue Jan 14, 2025 12:03 am
i have the wifi radio disable in the BIOS however the kernel update is installing drivers for it. is this normal?
Code: Select all
Building module:
Cleaning build area...
./dkms-make.sh...........................
Signing module /var/lib/dkms/8812au/5.13.6/build/8812au.ko
Cleaning build area...
8812au.ko:
Yes, it is normal as long as you have that driver installed.
You can remove wifi drivers that your system doesn't use with MX Cleanup.
this is what i came across the web about 8812au.ko
One of the best chipsets that support monitor mode and packet injection for both 5Ghz and 2.4 Ghz frequencies is the RealTek RTL8812AU, this makes adapters with chipset ideal for hacking, the only problem is this chipset is not natively supported by Kali Linux, therefore we need to install its drivers first before
Where did you read this nonsense? The rtl8812au driver covers a lot of wifi devices.
This is just a handful of them
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 3:00 am
by Stevo
DukeComposed wrote: Tue Jan 14, 2025 12:23 am
scatman98 wrote: Mon Jan 13, 2025 11:56 pm
good shape, except for the cache poisoning of apps via mitm attacks when running updates
You keep using that word. I do not think it means what you think it means.
Just movie quotes from now on.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 7:13 am
by scatman98
Well make of it what you will.
Here is the local IP rule set in the firewall to block the said IP but it is flowing both ways without issue.
Dnssec is setup
One site I use mattw.io won't resolve while all other sites resolve. This screen shot is from manjaro but the situation is same on mxlinux.
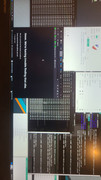
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 7:42 am
by Nokkaelaein
scatman98 wrote: Tue Jan 14, 2025 12:03 am
this is what i came across the web about 8812au.ko
One of the best chipsets that support monitor mode and packet injection for both 5Ghz and 2.4 Ghz frequencies is the RealTek RTL8812AU, this makes adapters with chipset ideal for hacking, the only problem is this chipset is not natively supported by Kali Linux, therefore we need to install its drivers first before
You are reading random stuff on the net and interpreting it in ways you do not have the technical qualifications for. That quote is from a so-called ethical hacker / penetration testing / security site advising how to install RTL8812AU support into Kali, saying RealTek RTL8812AU is ideal for hacking (as it supports monitor mode and packet injection in 5Ghz and 2.4 Ghz). Your quote doesn't mean it's an adapter that is ideal for an attacker to somehow hack into your computer when
your computer has it. It means the writer wants to point out this adapter is good when used in wireless pentesting, i.e. they opine it's ideal when
used for hacking.
At this point I think it's absolutely the most probable scenario that your exotic problems are all caused by the way you approach computing in general. You think of wild threats that are targeted at your system, then make dramatic adjustments to how your system works, without understanding how to do them, and as a result you break your system in various ways. Then you use that breakage as further proof that you have been attacked in various ways. It approaches actual paranoid thinking patterns. Note that your conceptions on several technical details have been corrected in this thread already, and even the title "Hacked by hydra" doesn't make any sense; you thought this was the case when merely seeing the package name "hydra", for a particular security tool, and reading it's got something to do with breaking passwords - and it turned out, even that package wasn't installed on your system. It's this same way of reacting to things and trying to "fix" them that gets you into problems in the first place.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 9:14 am
by DukeComposed
Nokkaelaein wrote: Tue Jan 14, 2025 7:42 am
You think of wild threats that are targeted at your system, then make dramatic adjustments to how your system works, without understanding how to do them, and as a result you break your system in various ways. Then you use that breakage as further proof that you have been attacked in various ways. It approaches actual paranoid thinking patterns.
"Approaches" is a generous way to put it. Let's not forget this thread began as "I've been hacked/Network tools I haven't installed must be malware", "No wait that's just normal apt search output", "sudo must be doing something wrong/I need apt-transport-https because I don't know repos GPG sign their packages/My cache is poisoned", "A common wireless driver is an exploit vector" and (my personal favorite) "I install a VPN by literally piping a random script to sh".
Out of all of these, "curl https:// something.sh | sh" is by far the most dangerous and it's the one thing that wasn't even slightly questioned by OP. Terry Pratchett once wrote "They say a little knowledge is a dangerous thing, but it's not one half so bad as a lot of ignorance."[0] I think learning the difference between security tools and malware, and that some people depend on Linux being easily hackable/malleable/"able to be made to do fun and clever things" is a good takeaway here and we should leave it at that.
[0] Not a movie quote. Apologies, the only relevant movie quote that comes to mind right now is about Santa Claus, the Easter Bunny, and a $100 bill from
Chasing Amy (1997) and it's NSFW.
Edit: typos
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 9:32 am
by Nokkaelaein
DukeComposed wrote: Tue Jan 14, 2025 9:14 am
Out of all of these, "curl https:// something.sh | sh" is by far the most dangerous and it's the one thing that wasn't even slightly questioned by OP.
Agreed. When I saw that I was going to comment exactly this

, then I figured it basically adds fuel to the fire, eh. But yes, so much ^ this. It's extremely telling that someone is so worried about very esoteric threats, convinced of being the victim of several different man-in-the-middle attacks, blabla, and then doesn't think twice about
piping to sh straight from curl.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 9:46 am
by siamhie
Stevo wrote: Mon Jan 13, 2025 12:28 pm
Captain America was pretty good at fighting Hydra...
So was Phil Coulson (Agents of S.H.I.E.L.D.).
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 9:54 am
by DukeComposed
Nokkaelaein wrote: Tue Jan 14, 2025 9:32 am
It's extremely telling that someone is so worried about very esoteric threats, convinced of being the victim of several different man-in-the-middle attacks, blabla, and then doesn't think twice about
piping to sh straight from curl.
My favorite anecdote about this is Etienne Millon, who wrote a blog post called "
On the curl | sh pattern" in 2014 and linked to a dedicated, era-obligatory
Tumblr page he'd created just to name and shame the installers that do this.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 9:59 am
by Eadwine Rose
Guys.. can we stick on topic, please. :)
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 11:23 am
by scatman98
Eadwine Rose wrote: Tue Jan 14, 2025 9:59 am
Guys.. can we stick on topic, please. :)
+1 i'm on a vpn which is working out for now.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 11:38 am
by Eadwine Rose
Good to hear :)
Please click the checkmark in the top right of the post (to the left of the username/user image) that holds the solution to mark the topic solved, thanks.
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 4:04 pm
by MXRobo
Time to close this topic. ?
Amber!
What's for lunch? Carpit?
- Not today.
Your mam's getting it shampooed.
===============================
The minute school is over,
I am out of here.
This place will kill you.
Where are you gonna go?
London.
I'm going to open
an anarchist bookshop,
- - but with franchise potential.
- Dating Amber
Re: Hacked by hydra. At wits end.
Posted: Tue Jan 14, 2025 4:12 pm
by Eadwine Rose
@MXRobo The request counts for you as well.
Re: Hacked by hydra. At wits end.
Posted: Wed Jan 15, 2025 12:30 pm
by Stevo
Before it get locked! The mod's got her slappin' fish out!
[0] Not a movie quote. Apologies...
Say WHAT?!? ZOMG!
You have disrespected
The Princess Bride. Prepare to die.

Re: Hacked by hydra. At wits end.
Posted: Wed Jan 15, 2025 12:36 pm
by j2mcgreg
Since the OP has reported that a kernel upgrade solved the problem, this topic is now locked.




